2Feb

HPからZBookの新しいBIOS Ver.1.42(sp85046)の配布が始まった。CPUのサイドチャンネル解析また投機的実行と呼ばれるCPUアーキテクチャの脆弱性問題に対応したIntelのマイクロコード更新を含んだBIOS Ver.1.41を適用すると、ブルースクリーンや再起動が頻発した問題の対策をしたIntelの新しいマイクロコードを含まれる。
新しいBIOS(Ver.1.42)への更新プログラム(sp85046)をダウンロードして起動すると
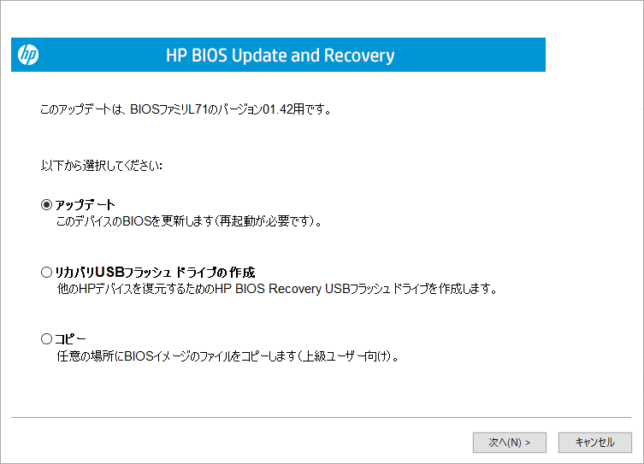
アップデート方法の選択になるので、通常は「アップデート」を選ぶ、「次へ」をクリックする
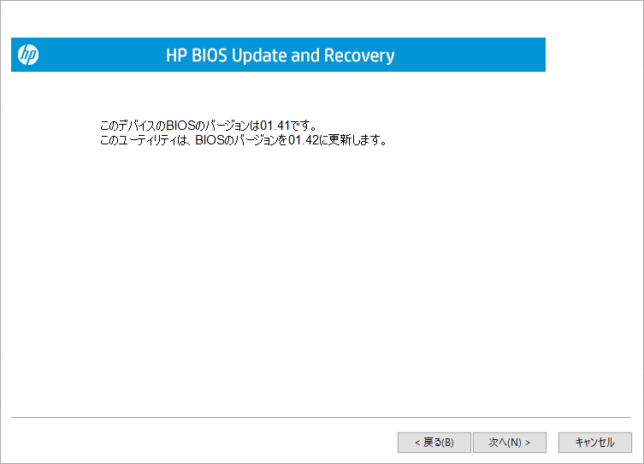
現在のBIOSバージョン(Ver.1.41)とアップデートするBIOSのバージョン(Ver.1.42)の確認になるので、「次へ」をクリックする。
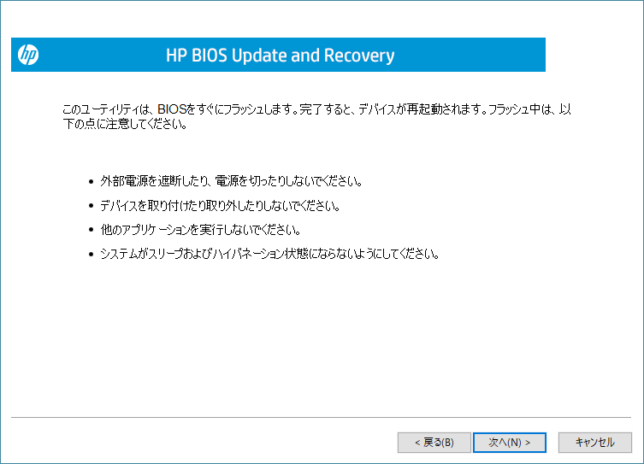
続いてBIOSを書き換える際に、アップデートが終わるまでACアダプターを接続し、電源を手動で切ったり、周辺機器を接続したり、他のアプリケーションを実行したり、システムがスリープや休止状態にならないようにといった注意事項が表示される。確認したら「次へ」をクリックする。
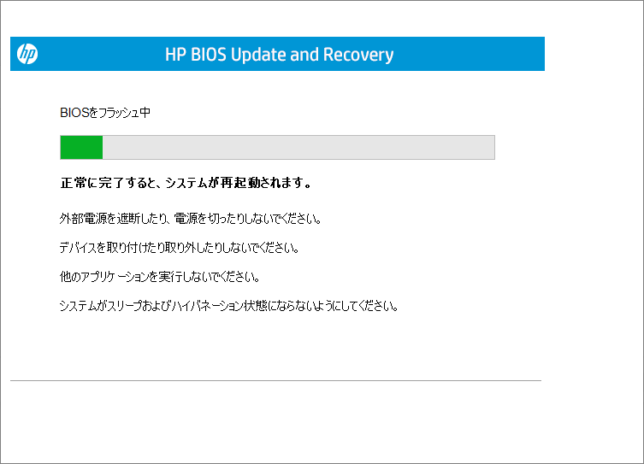
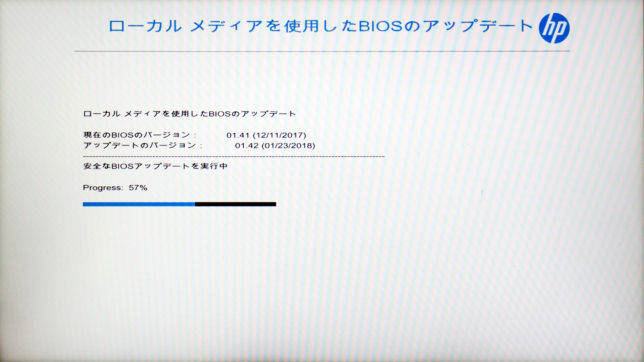
新しいBIOSを書き込み後、自動で再起動する。
再起動した後、BIOS更新作業が開始される。書き換え完了後、再起動すると新しいBIOSのVer.1.42へ更新が完了する。
これでCPU側の対応は完了だが、先日MicrosoftのWindows Update「KB4073119」で脆弱性対策部分を無効化しているので、その部分をレジストリで有効に変えないと本来の対策済みにはならない。
以下はその辺の情報。
Verifying that protections are enabled
To help customers verify that protections are enabled, Microsoft has published a PowerShell script that customers can run on their systems. Install and run the script by running the following commands.
Note These verification steps only apply to Windows client and not to Azure instances. For further cloud guidance, see the Azure blog.
| PowerShell Verification using the PowerShell Gallery (Windows Server 2016 or WMF 5.0/5.1) |
| Install the PowerShell Module
Run the PowerShell module to validate the protections are enabled
|
| PowerShell Verification using a download from Technet (earlier operating system versions and earlier WMF versions) |
| Install the PowerShell Module from Technet ScriptCenter.
Go to https://aka.ms/SpeculationControlPS Download SpeculationControl.zip to a local folder. Extract the contents to a local folder, for example C:\ADV180002 Run the PowerShell module to validate the protections are enabled Start PowerShell, then (using the example above) copy and run the following commands:
|
The output of this PowerShell script will resemble the following. Enabled protections appear in the output as “True.”
PS C:\> Get-SpeculationControlSettings
|
Switch | Registry Settings
Important This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
Note By default, this update is enabled. No customer action is required to enable the fixes. We are providing the following registry information for completeness in the event that customers want to disable the security fixes related to CVE-2017-5715 and CVE-2017-5754 for Windows clients.
| To enable the fix *
Restart the computer for the changes to take effect. To disable the fix *
Restart the computer for the changes to take effect. (There is no need to change MinVmVersionForCpuBasedMitigations.) |
* Note setting of 3 is accurate for both enable/disable settings due to masking.
Disable mitigation against Spectre Variant 2
While Intel tests, updates, and deploys new microcode, we are offering a new option for advanced users on impacted devices to manually disable and enable the mitigation against Spectre Variant 2 (CVE 2017-5715) independently via registry setting changes.
If you have installed the microcode, but want to disable CVE-2017-5715 – Branch target injection mitigation due to unexpected reboots and/or system stability issues, use the following instructions.
| To disable Variant 2: CVE 2017-5715″Branch Target Injection”:
To enable Variant 2: CVE 2017-5715 “Branch Target Injection”:
|
Note disabling and enabling the Variant 2 via registry setting changes will require a reboot and administrative rights.

|

【送料無料】【中古】HP HP ZBook 14 G2 (G8W46AV#ABJ) 【Windows7】 [中古ノートパソコン本体] |

【3年保証】 中古パソコン HP ZBOOK 14 G2【Windows10 Pro MAR】 [Core i7/Windows 10 Pro/ノート] |